SSL Acceleration on RiOS 6.0
Posted On Apr 26, 2010 at at 4:20 PM by DophiSSL acceleration is a function since RiOS 4.x and Riverbed continues to simplify the deployment and improve performance. On RiOS 6.0, SSL acceleration configuration is no longer as complex as previous version. Therefore, it can be done through a few steps. Here is a note for In-path SSL acceleration configuration.
1. Install SSL acceleration licenses on Steelhead’s: The Enhanced Cryptography License Key is not installed by default. In order to enable SSL acceleration, a license key is required and can be obtain from Riverbed. The link is https://sslcert.riverbed.com/
2. Setup SSL secure vault password on the client and server-side Steelhead appliance.
3. Import a proxy certificate and private key for the SSL server on the server-side Steelhead: Generate a certificate and private key in PKCS12 format from the SSL server. The extension name of the certificate should be PFX and it contains a decryption password.
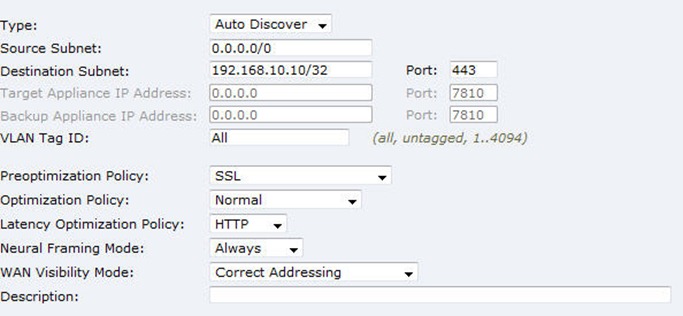
4. For client-side Steelhead appliance, add a new in-path rule:
- Specify the exact SSL server IP address and the default SSL port 443 for destination subnet and port.
- Setup Preoptimization Policy as SSL
- Latency optimization is not always HTTP, especially for applications that use SSL protocol but are not HTTP based. For those cases, choose “None” for the latency optimization.
5a. Configure SSL peering trusts on both client and server-side Steelhead:
- On the client side Steelhead, we can either copy certificate in PEM format or export and save it as a file with ”.bin” extension.
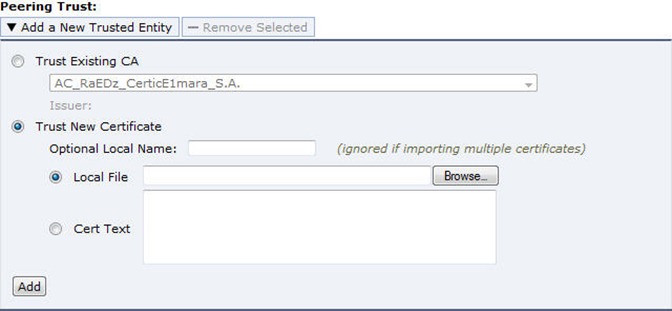
- Use the certificate copied or exported from client side Steelhead to create a trusted entity on server side Steelhead
- Select “Trust New Certificate” , either choose certificate from local computer or paste the copied certificate into the Cert
Text box. - Repeat the same steps on server side and import the server side certificate into client side Steelhead.
6a. Discover Steelhead appliances using self-signed certificates: Initial a HTTPS session and send traffic pass-though server side Steelhead. Steelheads will automatically discover the peers and place them in the self-signed peer white list.
An alternative way for Steelhead peering trust: This is a fast way to make peering trust in an environment with many Steelheads
5b. Discover Steelhead appliances using self-signed certificates: Initial a HTTPS session and send traffic pass-though server side Steelhead. Steelheads will automatically discover the peers and place them in the self-signed peer gray list.
6b. Manually add Steelheads to self-signed peer white list: On the drop down menu, choose “Trust” in order to move the peer Steelhead to white list. This should be done on both sides.
Before Trust:
After Trust
7. Import the internal CA certificates on server-side Steelhead:
- If we can’t get or import the CA-certificate from the back-end server or the server doesn’t verify for some reason, we can disable the back-end server verification by the command : (config)# no protocol ssl backend server verify