Alteon Switched Firewall 6000 Installation - Part 1
Posted On Oct 24, 2008 at at 2:33 PM by DophiNortel Switched Firewall (NSF) combines an appliance and Alteon switch to be a firewall that provides high performance inspection and brings the throughput up to 5.0 Gbps for the 6416 and 7.0 Gbps for the 6616. In the official document, the appliance is called as Director and switch is Accelerator. NSF director uses a single-system-image (SSI) as the main OS. This OS is used in other Nortel appliance as well, so it's easy to understand the concept if you are familiar with Nortel SSL VPN or Wlreless 2250. In addition, NSF accelerator uses a simplified Alteon OS. But, actually, this design also makes maintenance and troubleshooting be complex because we have to know how to use two different platforms and which function belongs to which one.
Recently, I create a lab test in order to transfer a old firewall to NSF and would like to note the procedures of installation of NSF. The platform is NSF 6614 running CheckPoint NGX R65 in my lab.
Topology:
VLAN 2: 20.0.0.0/8 ; The external VLAN leading to Internet
VLAN 3: 30.0.0.0/8 ; Internal
VLAN 4: 40.0.0.0/8 ; Internal
VLAN 5: 50.0.0.0/8 ; Internal
1. Initialize the major NSF: On this step, we have to create the IP address and Management IP (MIP)
[Setup Menu]
join - Join an existing NSF cluster
new - Create a new NSF installation
restore - Restore this SFD from a backup
offline - Configure this SFD for offline maintenance
boot - Boot Menu
naap - Set NAAP VLAN id
exit - Exit
>> Setup# new
Setup will guide you through the initial configuration of a new NSF cluster.
Enter an IP address for this SFD: 10.1.1.1
Enter a network mask or /bit count [255.255.255.0 or /24]: /24
Configuring and bringing up eth0...ok.
Enter the cluster Master IP address (MIP): 10.1.1.5
Checking if MIP is already in use...ok
2. Setup the time zone and time:
Timezone setting
1 - Africa
2 - America
3 - Antarctica
4 - Arctic
5 - Asia
6 - Atlantic
7 - Australia
8 - Europe
9 - Indian
10 - Pacific
Select a continent or an ocean, or enter a full timezone name: 5
Countries:
1 - United Arab Emirates 18 - Jordan 35 - Philippines
2 - Afghanistan 19 - Japan 36 - Pakistan
3 - Armenia 20 - Kyrgyzstan 37 - Palestine
4 - Azerbaijan 21 - Cambodia 38 - Qatar
5 - Bangladesh 22 - Korea (North) 39 - Russia
6 - Bahrain 23 - Korea (South) 40 - Saudi Arabia
7 - Brunei 24 - Kuwait 41 - Singapore
8 - Bhutan 25 - Kazakhstan 42 - Syria
9 - China 26 - Laos 43 - Thailand
10 - Cyprus 27 - Lebanon 44 - Tajikistan
11 - Georgia 28 - Sri Lanka 45 - East Timor
12 - Hong Kong 29 - Myanmar (Burma) 46 - Turkmenistan
13 - Indonesia 30 - Mongolia 47 - Taiwan
14 - Israel 31 - Macau 48 - Uzbekistan
15 - India 32 - Malaysia 49 - Vietnam
16 - Iraq 33 - Nepal 50 - Yemen
17 - Iran 34 - Oman
Select a country: 47
Selected timezone: Asia/Taipei
Enter the current local date (YYYY-MM-DD) [2007-10-23]:
Enter the current local time (24-hour, HH:MM:SS) [16:56:28]:
Setting the time...ok
3. Setup administrator's password, generate SSH key, and CheckPoint Secure Internal Communications (SIC) password: The one-time password entered here will be required later when establishing SIC between the SmartCenter and the Firewall Director.
Enter new admin user password:
Enter password again:
Generate a new ssh host key? ([y]/n) y
Enter Check Point SIC one-time password:
Enter password again:
4. Specify the Firewall Accelerator:
Supported Accelerators:
1) 6400
2) 6600
Enter the initial accelerator type (1, 2): 2
5. Configure the out-of-band management port: This step is not necessary but useful for management. I choose "N" because I don't need an individual management network in this topology.
Would you like to configure a management interface on FE1 port of the director?
This will provide a dedicated, out of band network for the Check Point
management server, Check Point GUI clients and WebUI clients ([y]/n): n
Starting SSI...ok.
Prepping SSI...ok.
Configuring Check Point.............................................................................................................................................................................Generating default filter
.............................................................................................................................ok
ssh v2 DSA host key signature is
45:b3:91:1b:15:fc:9c:ba:d8:62:9a:51:71:d5:ab:37
Setup successful. Please relogin to configure.
6. Enable ports: Port 5 connects to the edge switch with 802.1Q tag enabled. Port 8 is assigned as an Inter-Accelerator Port (IAP), Nortel Appliance Acceleration Protocol (NAAP) and VLAN tag must be enabled on it. The IAP is used for hear-beat health check and data forwarding.
>> Main# /cfg/net/port 5/ena
>> Port 5# /cfg/net/port 5/vtag y
>> Port 5# /cfg/net/port 6/ena
>> Port 6# /cfg/net/port 7/ena
>> Port 7# /cfg/net/port 8/ena
>> Port 8# /cfg/net/port 8/naap y
>> Port 8# /cfg/net/port 8/vtag y
7. Create VLANs and interfaces:
>> Port 8# /cfg/net/vlan 2/port/add 6
>> VLAN Ports# /cfg/net/vlan 3/port/add 7
>> VLAN Ports# /cfg/net/vlan 4/port/add 5
>> VLAN Ports# /cfg/net/vlan 5/port/add 5
>> VLAN Ports# /cfg/net/if 2/vlan 2
>> Interface 2# /cfg/net/if 2/addr 20.1.1.254
>> Interface 2# /cfg/net/if 2/mask 255.0.0.0
>> Interface 2# /cfg/net/if 2/broad 20.255.255.255
>> Interface 2# /cfg/net/if 2/ena
>> Interface 2# /cfg/net/if 3/addr 30.1.1.254
>> Interface 3# /cfg/net/if 3/mask 255.0.0.0
>> Interface 3# /cfg/net/if 3/broad 30.255.255.255
>> Interface 3# /cfg/net/if 3/vlan 3
>> Interface 3# /cfg/net/if 3/ena
>> Interface 3# /cfg/net/if 4/addr 40.1.1.254
>> Interface 4# /cfg/net/if 4/mask 255.0.0.0
>> Interface 4# /cfg/net/if 4/broad 40.255.255.255
>> Interface 4# /cfg/net/if 4/vlan 4
>> Interface 4# /cfg/net/if 4/ena
>> Interface 4# /cfg/net/if 5/addr 50.1.1.254
>> Interface 5# /cfg/net/if 5/mask 255.0.0.0
>> Interface 5# /cfg/net/if 5/broad 50.255.255.255
>> Interface 5# /cfg/net/if 5/vlan 5
>> Interface 5# /cfg/net/if 5/ena
8. Configure the default gateway:
>> Main# /cfg/net/route/gate/gw 1/addr 20.1.1.1
>> Default Gateway 1# /cfg/net/route/gate/gw 1/ena
9. Configuring the Firewall Accelerator: The Firewall Director can detect Accelerator automatically but I prefer to configure it manually because it might makes mistakes somehow.
>> # /cfg/acc
>> Accelerator Configuration# ac1/mac 00:1b:25:78:e1:00
>> Accelerator 1# addr 10.1.1.3
>> Accelerator 1# iap 8
10. Create Access List: This step is important but official document never mentions it. Without this step, NSF doesn't response everything except broadcast. The connection from SmartCenter is also rejected.
>> Main# /cfg/sys/accesslist/add 30.0.0.0 255.0.0.0
The NSF is ready for next step which is CheckPoint configuration.
Note: The VLAN ID of NAAP is 4094. This VLAN ID is also used on Standalone and SDM platform for NAAP.



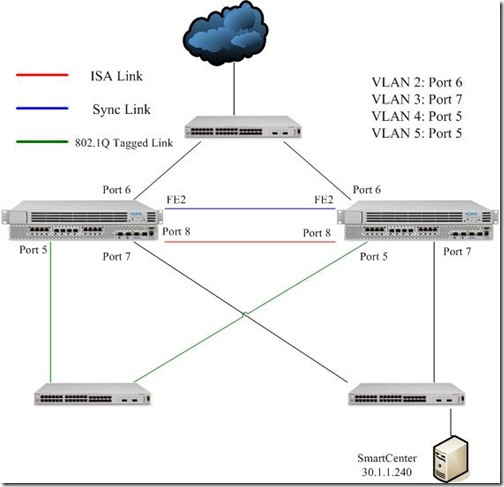

Why vlans?
Because there is a 802.1Q tagged VLAN in this topology. For the flexibility and development of this topology, I would like to assign an VLAN for each interface.